Wednesday, February 29, 2012
A Very Strange Mouse Issue
I started using the computer, and before long, I noticed one of the two thumb buttons wasn't working. I ran Counter-Strike Source and noticed that my flashlight was on when I first started playing the game (the key I used to turn on the flashlight happened to be my second mouse button). Then, I started VirtualBox and noticed that I couldn't click on any buttons or menus, although I could X out of the program.
I tried a different USB port and a different mouse, but nothing seemed to fix that problem. Then I remote desktoped into the system, and everything was working. Strange.
The next thing I tried was I completely uninstalled the drivers for my mouse, and then plugged in another mouse, and rebooted the computer. Everything worked.
I plugged my old mouse back in, and the problems came back. So I guess that was it - my beloved Logitech MX518 now has Mouse4 being pressed all the time, even when I'm not pressing it. So now I'm stuck with a cheap HP 2-button mouse, at least for the time being. (Why couldn't I have killed that one instead?)
Tuesday, February 28, 2012
NAT Routers
Remember telephone modems? You had to wait for your modem to dial in to your ISP, and once you were connected, it was agonizingly slow.
Typically with this setup, you have only one computer with a modem inside. When you dial into your ISP, a DHCP server assigns your modem a unique IP
address. This IP address identifies your computer and your ISP on the Internet.
Frustrated with these slow modem speeds, many telecom and cable companies began offering DSL and Cable modems, which are much faster than modems, and you never have to wait to dial in with them.
About this time, people also started getting new computers. Instead of having to fight over one computer, a family can have one computer for the parents and another for the kids. Now, what could be done to get both computers on the Internet?
The cable companies' solution was to sell you another IP address. That way, you could buy a switch, connect all your computers and your cable modem to the switch, and everyone could access the Internet at the same time.
However, consumers didn't like the idea of spending five, ten, or even as much as twenty extra dollars per month per additional IP address. So companies like Linksys and Netgear came out with routers.
How NAT Routers Work
A router allows several computers to share the same IP address and therefore connect to the Internet at the same time. Here is how it works:
- Every computer on the network is assigned a local (LAN) IP address by the router. These IP addresses are not unique and only apply to the LAN (local area network).
- The router has two IP addresses: a LAN IP and a WAN (wide area network) IP address. Computers on the LAN communicate with the router by connecting to its LAN IP address (the default gateway). Computers on the Internet communicate with the router's WAN IP address.
- When you request data from a server on the Internet, your router replaces your LAN IP address in the return header with its WAN address. Then, when the data comes back, it changes the return address back to your LAN IP.
This process is called network address translation, or NAT.
Separating Applications into Ports
Every computer (or router) has 65,535 ports. When one computer establishes a connection with another computer, it sends data to its IP and port. The other computer must be listening on the port the data was sent to for it to receive anything.
Established standards usually dictate which ports should be used for specific types of services. For example, HTTP services usually run on port 80. FTP services are usually on port 21, and America Online uses port 5190. Though these are the standard ports for these services, it is not a requirement to run those services on those ports. You could, for example, run an HTTP server on port 21 and an FTP server on port 80.
So, when two computers establish a connection, the client opens a connection with the server on a certain port.
How NAT uses Ports to Share a Single IP Address
Most of the time, the server will need to send data back to the client. So the client must also be able to accept connections on a port. Note that this does not need to be the same port that the server is listening on. In fact, it almost never is.
When the client sends a packet to the server, it specifies in that packet the IP address and return port of the client.
So let's see what happens when you access CNN.com. For this example, we'll assume your IP address is 192.168.0.1.
- First, your computer will find out the IP address of www.cnn.com from a DNS server.
- Next, it will request the file index.html from 64.236.24.12:80 (CNN's IP address, on port 80). The request packet also includes the IP address and port your computer is listening on for the file. We'll say it's 192.168.0.1:4000
- CNN will send index.html to 192.168.0.1:4000.
- The process will be repeated for pictures and other files that appear on index.html
The Caveat of NAT
What happens when someone behind a router is running a server? Well, if you try to open a connection with someone behind a router, the router won't know which of the possibly hundreds of computers connected to the router you want to open the connection with.
In this case, the router will do one of two things: it will either respond saying that the port you are trying to connect to is closed, or it will not respond at all. The latter case is called a filtered port. Filtered ports are supposed to be more secure because a machine with filtered ports takes much longer to port scan. This involves checking every port on the host to see which ports are open (and available to connect to, and try to hack).
Fortunately, there is a way around this limitation. And it's a good thing, too, since P2P applications work much better when you can accept incoming connections.
Most routers allow you to set up port forwarding. This means you can tell the router that you want incoming connection requests on a certain port to be forwarded to a specific IP address on your LAN. Check your router's documentation for details, or try this site.
If you are unable to set up port forwarding, you will still be able to connect to P2P networks since you can open connections with other hosts that have port forwarding enabled. However, in order for anyone to download from you, they will need to send something called a push request. The way this works is their client tells your hub/server to tell your client to open a connection to his computer.
Naturally, you cannot send a push request if you yourself do not have port forwarding enabled. So you will not be able to download from users who are behind routers (and they, of course, have the fastest connections).
Networking Basics
-----
A network is a group of computers that are connected together using cables or wireless networking technology. The Internet is a global network that connects many smaller networks together.
Types of Networks
A Local Area Network (LAN) is a network that typically consists of computers in a single building or location.
A Wide Area Network (WAN) is a network that consists of computers in many locations. They can be in different cities, different states, or different countries. The Internet is, and is almost synonymous with, a WAN.
Network Identification
Each computer on the Internet must be identified uniquely. This is done by using an IP (Internet Protocol) address.
IP Addressing
An IP address consists of four octets. Each octet is an 8-bit number from 0 to 255.
It can be denoted in dotted decimal notation: 192.168.100.70
It can also be denoted in binary: 11000000 10101000 01100100 1000110
Host Names
On a LAN, computers can also be identified by their computer name. This can be a 15 (maximum) character string consisting of alphanumeric characters and hyphens. For example, my computer name is Chris1.
On a WAN, host names must be used. A host name is a computer name plus a domain name. For example, Chris1.chapman.edu.
When you access network resources by providing a host name or a computer name, a special server called a name server or a DNS server looks up the IP address that is associated with the provided host name or computer name.
If you are using Windows and are not on a domain, computer names are resolved by sending a broadcast packet to the entire network. Whichever computer has the name you are attempting to resolve responds with its IP address when it receives the broadcast.
Dividing Networks into Subnets
Networks can be divided into subnets using a subnet mask. The subnet mask can be used in combination with an IP address to obtain the network address (or subnet address).
Recall that an IP address consists of 32 bits (four 8-bit octets). The subnet mask is simply a number from 0 to 32 that identifies how many bits of the IP address are used in the network address.
Subnet Mask Notations
The simplest way to denote a subnet mask is with a slash. A subnet mask of /24 indicates that the first 24 bits of the IP address are used to represent the network address.
Using the example IP address 192.168.100.70, 192.168.100.70 / 24 denotes the entire network that 192.168.100.70 resides on. By applying the subnet mask to the IP address, we can extract the network address. In this case, the network address is the first 24 bits, or the first three octets of the IP address. This works out to be 192.168.100.0.
Subnet masks can also be denoted in binary. A subnet mask of 24 looks like this: 11111111 11111111 11111111 00000000. If we denote an IP address and subnet mask in binary, performing a logical AND operation on the two will give us the network address:
11000000 10101000 01100100 01000110 (192.168.100.70)
& 11111111 11111111 11111111 00000000 ( /24 )
= 11000000 10101000 01100100 00000000 (192.168.100.0)
Subnet masks can also be represented in dotted decimal notation: 11111111 11111111 11111111 00000000 = 255.255.255.0 = /24.
Note that the network address is the first address of any subnet. It is reserved. Therefore, no computers on your network can be assigned to use the network address.
Uses for Subnet Masks
Suppose another computer has the IP address 192.168.100.73. If we apply a subnet mask of 24 to this IP address, we get 192.168.100.0 as the network address. Since the network address is the same as the network address of the above IP address, both IP addresses are on the same network.
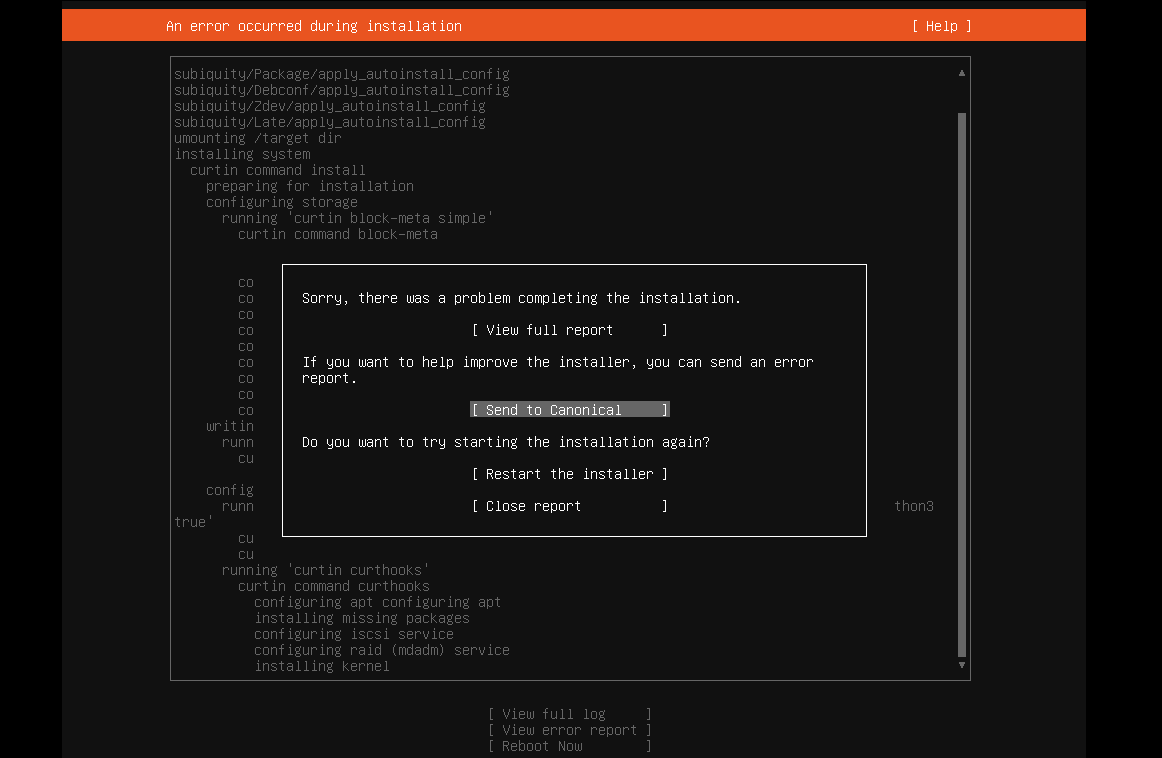
Ubuntu 22.04 on VMware Workstation Error
I tried installing Ubuntu 22.04 server on VMware Workstation and got this message: Sorry, there was a problem completing the installation E...
-
We have a customer at work that runs Dentrix. They have 4 offices, and need to have all of the patient data in one place. Unfortunately,...
-
There is an Android app included that will capture GPS coordinates from your Android device and save them to a file. Airodump CSV Tools will...
-
I tried installing Ubuntu 22.04 server on VMware Workstation and got this message: Sorry, there was a problem completing the installation E...

